Patch management is about identifying, acquiring, and deploying software updates. In particular, security patches are essential to address known vulnerabilities and minimize risk within your IT infrastructure.
But patching is a time-consuming job. Sometimes it can be weeks, even months, before a patch is applied where needed.
And this leads to significant problems.
Often, data breaches can be traced back to the same issue…
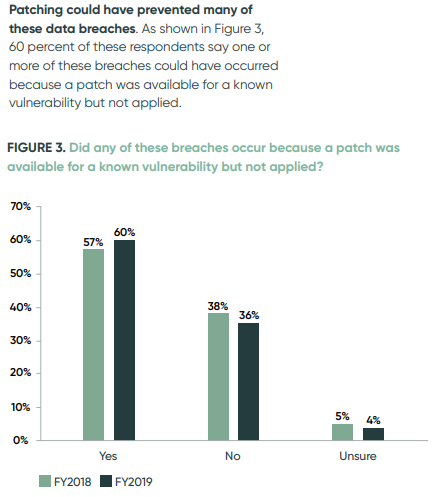
“Nearly 60% of organizations that suffered a data breach [reported] a known vulnerability for which they had not yet patched”. Kelly Jackson Higgins, Editor-in-Chief, Dark Reading
Managing this process for a remote or hybrid workforce introduces unique challenges that require careful consideration and planning. As well as dedicated tools to help roll out patches automatically when available.
This guide is to help IT professionals tackle patch management at scale for an on-site, remote or hybrid workforce.
How to create a patch management strategy
STEP 1: WHEN SHOULD YOU PATCH AND WHAT TO PATCH FIRST
Your strategy must be tailored to your company’s specific needs and systems.
So 2 key things to consider are: frequency and priority.
- Frequency
A good starting point would be to map out each software vendors’ recommended patching schedules. For example, we all know about “Patch Tuesday“, when vendors like Microsoft and Oracle release updates in North America.
Of course, not every vendor will have a regular schedule like this. And there will always be hot-fixes or urgent, unexpected releases in response to a new vulnerability discovered. But planning around what is expected every month helps carve out room for patches that “come from nowhere”.
And it’s important that you do, because those are usually security-critical.
- Priority
The reality is, you and your team have finite resources.
In an ideal world, every patch would be treated as “urgent” and actioned straight away. That’s not possible for most IT teams, working under pressure with a lot of plates to keep spinning.
How do you decide which patches get priority?
a) How critical they are to day to day operations
b) How exposed your company’s data would be if the system was compromized
If a system went down how much of a disruption would it be? And what data would be at risk if the system was breached?
A live inventory of software, servers, workstations, devices, and so on, is essential.
Rank them based on how critical they are, the type of the data they hold, and their role in live business operations.
STEP 2: WHAT PROCESS DO YOU FOLLOW?
You know which patches take priority, and you know roughly how often to expect them.
How will you action them? Like any good process, it must be repeatable time after time.
- Test patches in a controlled, staged environment
Before deploying patches, test them in a controlled environment that mirrors your production environment.
This testing phase helps identify conflicts or performance issues before they affect something negatively. You’re looking out for patches which are not compatible with existing software and applications.
After all, we want to minimize unexpected consequences.
From the test environment you can move onto less crticial servers. Monitor these deployments closely to ensure patching success and to address any unforeseen issues promptly.
Gradually extend the deployment to critical systems, verifying each step along the way.
- Leverage patch management tools
As noted earlier, human error or inaction, is often what allows vulnerabilities to be exploited. Don’t take that security risk.
Utilize patch management software or tools to automate the process and streamline patch deployments.
What are you looinking from a vendor in this space? Features and functionality to centralize patch management, schedule deployments, and monitor patch compliance across your systems.
STEP 3: MONITOR AND VERIFY PATCH COMPLIANCE
- Understanding your compliance requirements
Patch compliance refers to whether or not devices on a network have received and installed updates. It takes in account an ability to detect and deploy patches.
But it’s also about your ability maintain visibility into endpoints, and ensure overall software and hardware are up to date.
Various standards like PCI DSS, HIPAA, NIST, and GDPR, consider patch compliance a crucial aspect of your overall compliance status.
For companies with remote and hybrid workers, where IT teams can’t manually check or enforce an update, this can be challenging.
But a good unified endpoint management solution should allow you to pinpoint which endpoints are running outdated software or firmware. This is the only way you can maintain a secure and up-to-date environment.
- Establish an incident response plan
Even with an effective patch management strategy, security breaches can occur. An incident response plan to address potential breaches or incidents resulting from unpatched security vulnerabilities.
This plan should outline steps for isolating affected systems, conducting forensic analysis, and applying emergency patches or workarounds.
Patch management is an ongoing process. Review and improve your patch management procedures based on feedback, lessons learned, and emerging best practices. Stay vigilant in assessing the evolving threat landscape and adapt your strategies and tactics accordingly.
Simplify patch management with ThinScale
Patch deployment can be complex, especially in large IT environments with 100s and 1000s of devices. A remote or hybrid workforce further complicates things. As does a high percentage of 3rd party contractors accessing your virtual network.
ThinScale specializes in unified endpoint management for enterprise estates. We simplify things likes patch management for IT teams trying to achieve more with fewer resources.
As part of ThinScale’s powerful UEM solution, IT teams are given increased control over Windows patches, and complete control over any 3rd party software.
Further, with advanced access policies, Windows patch management features, and device analytics – IT teams gain full visibility over the status of endpoint security status, Windows patch status, and even the version of any application installed on your endpoints.
With this information you can deploy software and updates exactly where they are needed. ThinScale allows IT to package and deploy any software to any endpoint, centrally. This includes vital security updates for LoB software. The software being deployed is installed in minutes and can even be scheduled to install on the next user-login to the secure workspace, ensuring as little disruption as possible while patching.



