Securing endpoints without breaking application compatibility or simply affecting productivity is an ongoing challenge for modern IT departments. Often, concessions must be made, either by restricting or losing app functionality or loosening security protocol and making exceptions for vital LoB apps. Striking the perfect balance between robust security policies and workload requirements is crucial.
ThinScale’s Process Security empowers IT teams to achieve this delicate balance, ensuring a highly secure endpoint environment without compromising operational efficiency, providing security and flexibility.
Exploring ThinScale’s Process Security
Process Security Overview
ThinScale’s Process Security is a collection of rules, settings, and system protections designed to fortify any ThinScale endpoint. At its core, this engine allows IT teams to establish rules for processes based on the relationships between preceding and succeeding conditions.
Beyond the traditional blacklisting and whitelisting, Process Security extends its reach to Process Access, Thread Access, and Volume Access.
Benefits of Process Security
Endpoint environments are diverse, with varying application and action requirements based on roles, departments, or even individual users. Process Security caters to this diversity, allowing IT teams to implement tailored security measures.
Whether it’s restricting access for specific teams or granting selective permissions for crucial applications, Process Security ensures a nuanced approach to endpoint security and flexibility. This adaptability guarantees that vital applications run seamlessly, preserving the integrity of the entire secure infrastructure.
Setting up a Rule
In this example, we want to allow only 2 specific versions of an application based on filename and sizes, while denying anything else that may attempt to run or access our end-user’s machine.
First, we will add a condition to verify the filename. Here, we assign our application name and file path under the “image name” dropdown.
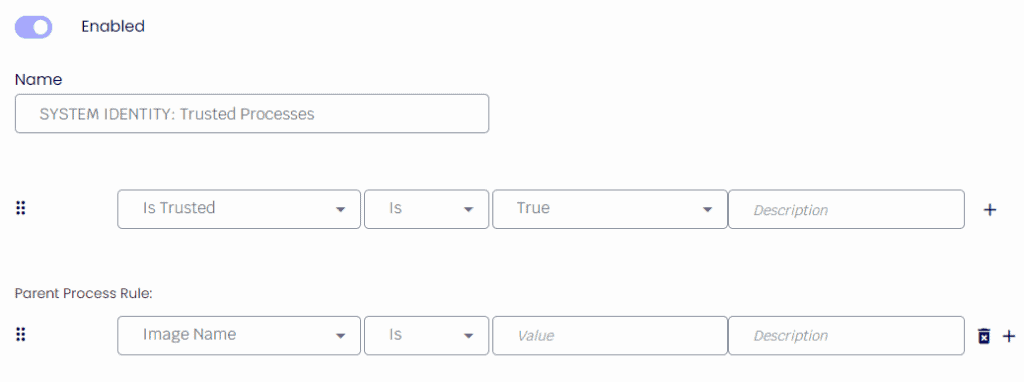
After we will allow 2 possible file sizes – to do this, we just need to add another condition, choosing “and” followed by “file size”, and then specifying the file size. We then create a new “or” condition followed by “file size, specifying the other file size.
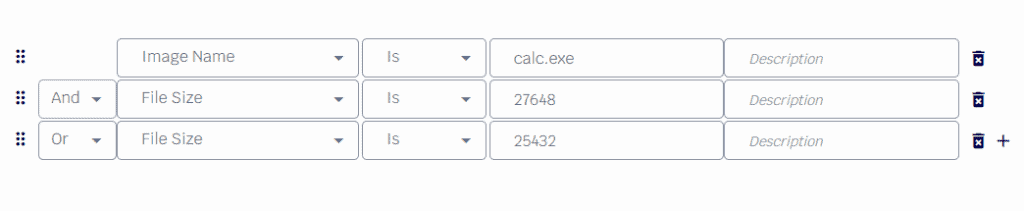
This set of rules will perform checks on any process attempting to run and will only allow a process to run if it matches the specified file name and one of two specified file sizes.
In this example, the first condition involves verifying the filename. Subsequently, two conditions for file size are introduced using logical operators “and” and “or”.
By specifying the file sizes, IT teams create a rule that allows the process to run only if it matches the designated filename and one of the specified file sizes. This meticulous approach to rule creation showcases how IT can fine-tune process and application whitelisting to align with their specific use cases.
Learn More
For an in-depth understanding of Process Security and its key features, our administrator’s guide can be accessed here.
Or get in touch to learn more about Process Security and how it can be tailored to your specific use case.



