What is BYOD?
PArt 1
WHY?
Why should you adopt a secure BYOD model?
Reduced hardware & logistics costs
Business Continuity
Faster sale-to-seat process
Improved employee experience & productivity
Calculating the true costs of corporate devices vs. BYOD
How much is your organization really spending on corporate devices year on year?
When you factor in depreciation and amortization, the cost of replacing lost/ stolen/ damaged devices, the transportation costs, and so on, alongside the upfront cost of each device, the true cost is eye-watering.
That’s why we created a calculator to account for all these variables and put a figure on exactly how much your organization could (and in our opinion, should) be adding to your bottom line.

Download the full PDF of our Guide to Secure BYOD for more on aligning various departments for a successful deployment
PArt 2
HOW?
How do you make BYOD work for your organization?
The criticality of cross-department integration
The most successful BYOD implementations that we’ve seen have been a collaborative effort between IT, HR, or Operations, with senior leaders working together to align the entire organization on every aspect from security to hiring and employee experience.
Below is an example of what might be expected of IT, HR, and Ops teams:
Operations
- Create a repeatable process for onboarding BYOD candidates, with all necessary documentation and training materials
- Create a repeatable process for IT / support to remediate any candidates with minor hardware issues
- Oversee a shared project plan, with clear timeframes across each business unit
IT/Support
- Define the baseline hardware specs required for each line of business
- Create process or self-help documentation for Validation Tool warnings or failed results
- Provide Validation Tool results directly to talent acquisition team to evaluate and qualify candidate pool
HR/Talent Acquisition
- Create a job posting that identifies the role as a BYO-only opportunity
- Include clear, detailed set of baseline hardware specs in posting (we give an example later)
- Embed a link to ThinScale’s validation tool into the job posting and require candidate to validate the suitability of their device before application is processed

Helping you onboard BYOD employees at Speed & Scale
Device Validation Tool
ThinScale’s Validation Tool allows you to pre-vet the suitability of a candidate’s device before they are invited to the interview stage. This enables hiring teams to focus only on candidates that have hardware which meets the baseline requirements for a particular line of business.
The Validation Tool can also determine the quality of the network connection, alerting you if there’s a potential issue with a candidate’s internet set-up that could limit their capacity to work online.
Download the full PDF version of our Guide to Secure BYOD for a deeper analysis of the benefits of BYOD and cost-savings it creates.

PArt 3
WHAT?
What do you need to make BYOD secure?
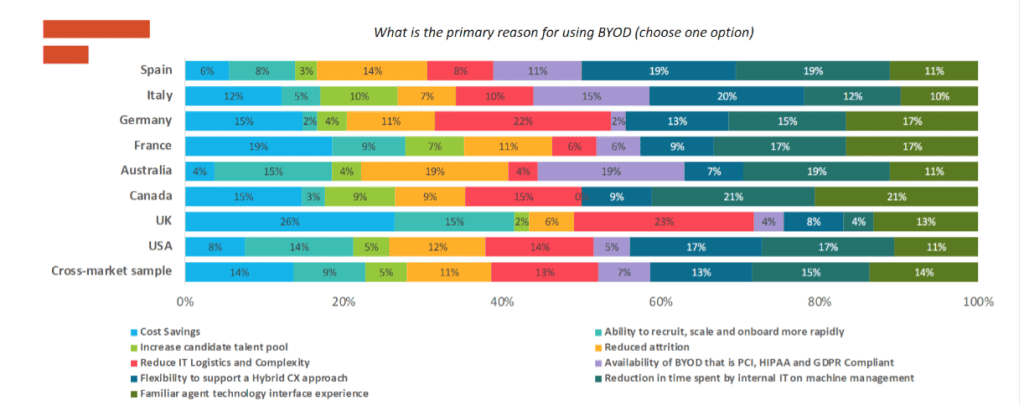
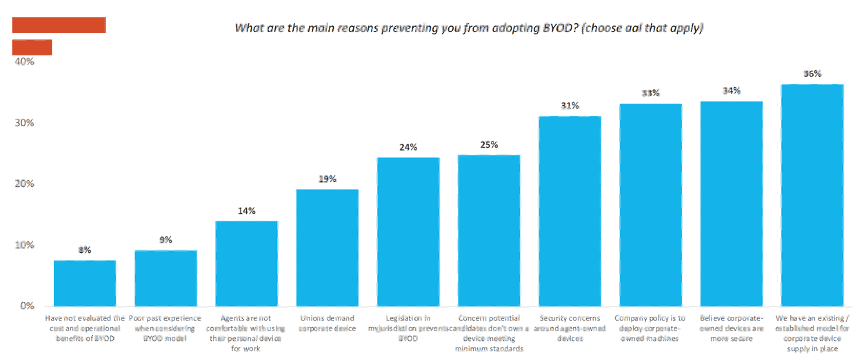
Looking at the 2022 Ryan Strategic Advisory CX Omnibus Report, security accounts for a combined 64% of c-suite responses to the question: What are the main reasons preventing you from adopting BYOD.
Security & IT leaders are asking:
“How can we control and secure these BYOD/ untrusted devices to same standard as our corporate-owned devices, given that we don’t own them?”
The key to secure BYOD is getting control and visibility over the “untrusted” device to consistently enforce strict access policies, remotely image and wipe, and ensure all apps and firewalls are up to date.
Employer Concerns Vs. ThinScale Solutions
Unprotected wifi networks
ThinScale Solution:
ThinScale prevents a user from launching a secure session if the device is connected to an unrecognized or insecure network connection. It can even enforce an ethernet connection, if so desired.
Updating & Patching
ThinScale Solution:
IT teams can remotely distribute and update software packages across the entire estate, automatically downloading and installing before a secure session can be opened.
Employees' privacy rights
ThinScale Solution:
ThinScale ensures segregation between corporate and personal environments. Once a secure session is ended, the IT team has no control or visibility over the personal device, which is restored exactly as it was before the secure session launched.
Client data loss or leakage
ThinScale Solution:
Dual Persona technology to create separate and encrypted users, only accessible via a ThinScale login, to prevent unauthorized access or data loss.
Client data loss or leakage
ThinScale Solution:
IT teams can remotely uninstall ThinScale from the device, removing access to corporate data when an employee’s contract ends.
3rd party software attacks
ThinScale Solution:
ThinScale’s AEP (Application Execution Prevention) technology prevents unauthorized programmes (e.g. malware) from running while a secure session active.
